Learn to spot phishing scams
Kotler Law Firm P.L.
For more information about the author, click to view their website: Siena Wealth Advisors
Jul 22, 2023
Florida - Southwest
Email US
Click to Email UsPhishing attacks are phony communications designed to trick a person into giving a scammer sensitive or financial information, such as account usernames, passwords, credit card information and Social Security numbers.
Phishing attacks may appear to be from a legitimate business or trusted individual and can come in many forms – email, text message or phone call – so it’s imperative to understand the red flags associated with these malicious attempts.
Remember: If a message – whether it be email, text or phone – appears suspicious in anyway, don’t engage.
Here’s how to better protect your account from these different types of phishing attacks:
- Email phishing
- Text message phishing
- Voice call phishing
Email phishing
Email phishing refers to fraudulent emails that typically appear to come from trusted individuals or legitimate businesses such as financial institutions, insurance companies or retailers and often include seemingly authentic logos, look-alike email sender domains, as well as links or graphics that look genuine.
Fraudsters engaging in email phishing may attempt to deceive you into downloading an attachment or clicking on a link within the message that will download malware onto your computer to illicitly obtain personal and financial information. These links may also redirect to legitimate portals, such as Microsoft Office, where they will ask you to enter your account credentials.
What to watch for:
Sense of urgency. Phony phishing messages try to ‘bait’ you with an urgent situation requiring you to take immediate action. Watch for clickable links to ‘update’ or ‘validate’ personal information. Additionally, be cautious of any emails that appear to use current news events (like a natural disaster or geopolitical tumult) to solicit donations.
Spelling or grammatical errors. It’s rare for a well-known company to have spelling and grammatical errors.
Suspicious links. Be wary of links in emails. It’s always safest to go directly to the company website and log in to your account.
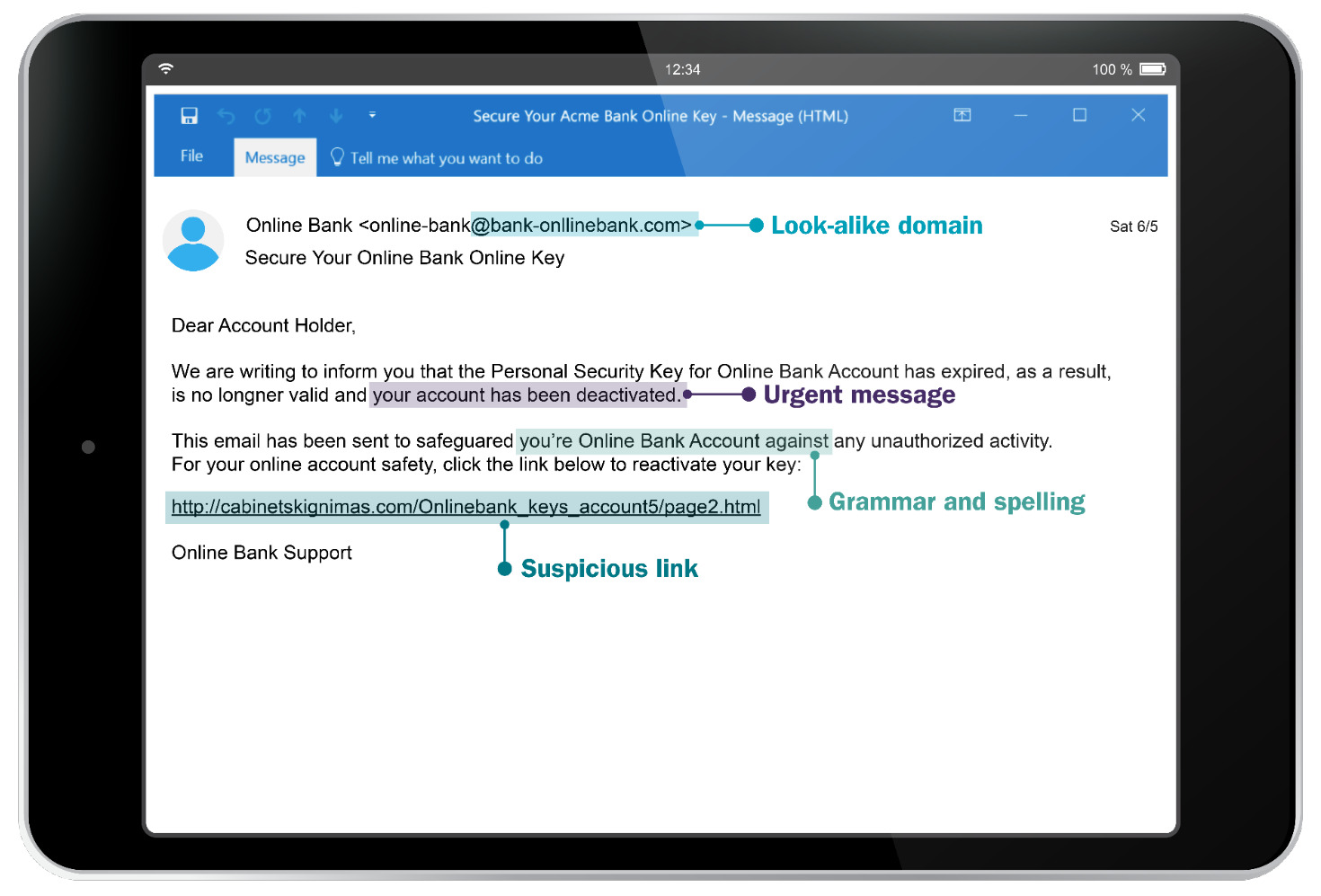
What to do if you suspect an email is a phishing scam
- Do not click on any attachments or links in the email, or take any action requested within the message.
- If the email is sent to a work account, follow their protocol for reporting phishing attempts.
- If the email is sent to a personal account, delete it and follow up with the purported sender directly. For example, if the sender appears to be a company, visit the company’s website directly to check on your account activity.
- Log in to accounts using 2-Step Verification when possible.
How to report email fraud or phishing to Ameriprise
If you suspect you’ve received a fraudulent email from someone posing as Ameriprise, please:
- Forward it to us immediately at: anti.fraud@ampf.com.
- Do not remove the original subject line or change the email in any way when forwarding.
- Watch for an auto-generated reply to let you know we’ve received your email. If we confirm the email is fraudulent, we will take appropriate action immediately.
- If you provided your account information to a request you suspect may have been fraudulent, call us immediately at 800.862.7919.
Text message phishing
Text message phishing – also known as “smishing” – refers to fraudulent messages sent via text or through other mobile-friendly communication platforms, such as Instagram direct messages, WhatsApp or your LinkedIn mailbox. Like email phishing, scammers conducting text phishing attacks aim to steal their victims’ personal and financial information.
What to watch for:
- Fake email address. Most companies use a short code to send text alerts, not an email address. Emails may be from a look-alike domain and not a legitimate firm or company.
- Suspicious links. The URL should include the company name and website domain (ameriprise.com, for example). Always be cautious of shortened URLs from services (bit.ly or tinyurl.com, for example).
- Urgent or threatening message. Messages are written to try to ‘bait’ you with an urgent situation that requires you to take immediate action. If the text contains a threatening message, it’s probably a scam.
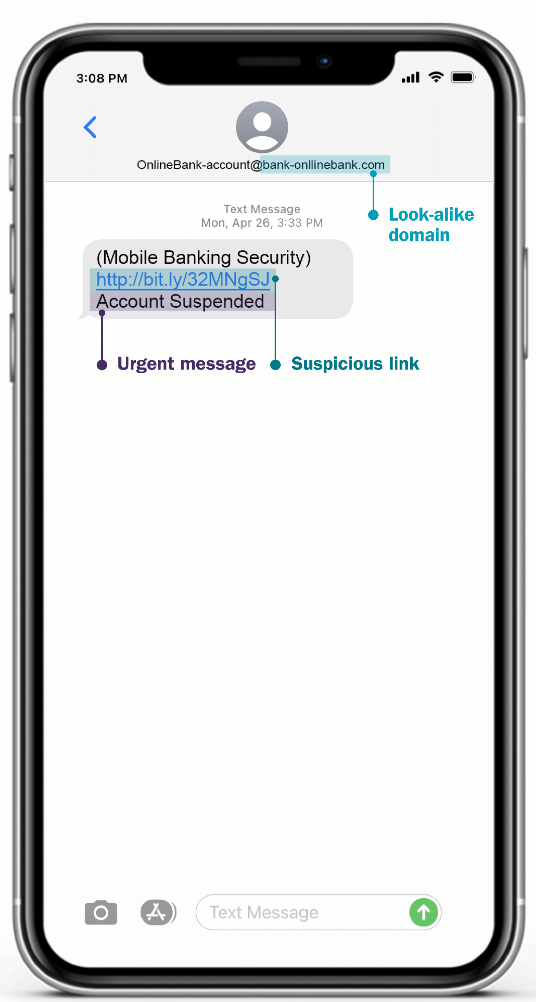
What to do if you suspect a text phishing scam
- Be wary of links sent through text messages.
- If the text message seems suspicious, do not respond.
- Visit company websites directly to check on your account activity.
Voice call phishing
Voice call phishing (also known as “vishing”) is when a fraudster attempts to deceptively extract an individual’s personal or financial information through a phone call.
What to watch for:
- Personal information requests. Ameriprise Financial, government agencies, and other bank and financial companies will not call you unexpectedly and ask you to provide personal information like passwords, account numbers, or Social Security numbers.
- Remote access requests. Never give anyone remote access to your computer unless you have contacted them. Be wary of popups on your computer screen asking you to download software. Tech support from legitimate companies will not engage you this way
- ‘Local’ phone numbers. Phone numbers can be spoofed. Be cautious of unfamiliar phone numbers even if they appear to be local.
- Sense of urgency. Like in the case of email or text phishing, vishing messages try to ‘bait’ you with an urgent situation requiring you to take immediate action.
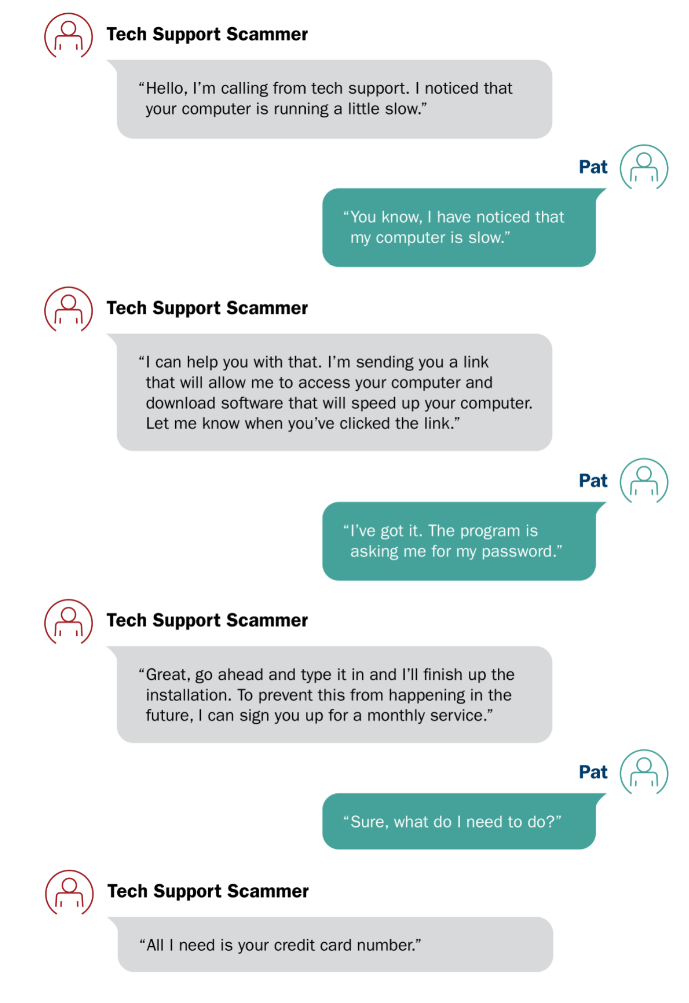
What to do if you suspect a phone call is a phishing scam
- Don’t answer. Let calls from unfamiliar numbers go to voicemail.
- Block phone numbers on your mobile phone that call repeatedly for a fake business reason.
- Be wary of links sent to you from the caller even if they seem like they are from a well-known company. Clicking links may allow the scammer to install spyware to your computer or device.
We're committed to protecting your information
At Ameriprise Financial, we’re committed to protecting your online security. Our efforts are backed by our Online Security Guarantee, which covers 100% of the value of losses in your Ameriprise® account(s) due to unauthorized online activity, if we conclude that losses were incurred from your account through no fault of your own.
For more information about the steps you can take to help protect your account and personal information, review How you can protect yourself in the Ameriprise Financial Privacy, Security & Fraud Center.
- To view the original version of this article visit www.ameriprise.com/privacy-security-fraud/identifying-phishing-scams
- Seniors Blue Book was not involved in the creation of this content.
Other Articles You May Like
Fraud Checklist: What to Do if Youve Been Scammed
You thought this could never happen to you or your aging loved one: the heartbreaking loss of a hard-earned life savings as a result of a scam.But the growing incidence of older adult fraud is putting many in harms way. Its important to know how to move forward if fraud does occur.Steps to Take if You or Someone You Know is Scammed Close your accounts. If you notice any accounts under your name or that of an aging loved one that have been tampered with or opened without consent, close them immediately. Contact the police. File a report with your local police department. If the theft did not take place in your area, file a report with the police from the area where you believe the theft took place. Get a copy of the police report. You may need that documentation to support your claims to credit bureaus, creditors, debt collectors or other companies. If you are unable to obtain a copy of the police report, be sure to get the report number. Eliminate fraudulent new accounts. If a new account has been opened without you or your aging loved ones knowledge and consent, ask the company with which the account has been opened if it has a fraud department. Initiate a fraud alert. Place a fraud alert on the credit file that has been compromised as well as review the credit report. This will prevent a thief from opening any more accounts in you or your loved ones name. You should contact the major credit bureaus. If you place a fraud alert with one credit bureau, that credit bureau is required by law to contact the other bureaus. Follow-up. After a fraud alert is included in the credit history, you or your aging loved one is entitled to receive a free copy of his or her credit report from each of the credit bureaus. Important Documents for Victims of ScamsThe following are important documents to keep on hand if youve been scammed. If your aging loved one won't be able to keep the originals of some of these important documents, it is important that you make a copy. Police report Identity Theft Affidavit Bills with fraudulent charges Documentation of accounts opened in your name without your consent Copies of letters sent to credit bureaus and creditors Credit bureau contact information: Equifax- 800-525-6285 Experian- 888-397-3742 Transunion 800-680-7289 (U.S.) 800-663-9980 (Canada) If you or your loved one is a victim of fraud, acting quickly is key. Begin working through the fraud checklist above as soon as possible to help minimize the damage.
What to Do If You Get a Voice Fraud Call That Is AI-Generated
Scammers are increasingly adopting new methods to deceive unsuspecting victims, especially older adults. One of the latest threats is AI-generated voice fraud, also known as vishing (voice phishing). These scams use sophisticated AI technology to create highly realistic voices that mimic trusted individuals or organizations.Lets talk about what you should do if you receive such a call and how to protect your sensitive information.Understanding AI-Generated Voice FraudAs mentioned, scammers perform AI-generated voice fraud using synthetic voices that sound convincingly like a family member, friend, or legitimate entity such as a bank or government agency. These calls can be exceptionally persuasive and dangerous since the synthetic voices replicate the speech patterns and tone of the impersonated individuals. Additionally, fraudsters can manipulate caller ID to make it look like the call is coming from a trusted source when it is not.Common Tactics Used in AI-Generated Fraud CallsBe on alert for the following AI-generated fraud calls:Impersonation of Family Members: Scammers may claim to be a relative in urgent need of money due to an emergency. The voice will sound distressingly familiar, making it easy to fall for the ploy.Bank Representative Scams: Fraudsters impersonate bank representatives, asking for account details or prompting money transfers to secure accounts.Tech Support Scams: Callers pose as tech support from reputable companies, convincing victims to grant remote access to their computers or pay for unnecessary services.Government Agency Impersonation: They may mimic officials from agencies like the IRS or Social Security Administration, threatening legal action or demanding immediate payment of fines or taxes.Utility and Phone Company Scams: Fraudsters imitate representatives from utilities or phone companies, claiming issues with the account and requesting payment or personal details to resolve them.Steps to Take If You Receive a Suspicious CallSo, what should you do if you receive such calls that are highly convincing? Here are some essential steps to take:Stay Calm and Dont Panic: Scammers often create a sense of urgency to pressure you into making quick decisions.Verify the Callers Identity: If the caller claims to be a family member, ask specific questions only that person would know. If the caller claims to be from a legitimate organization, hang up and call the organizations official number to verify.Never Share Personal Information: Legitimate entities like the bank or the government will never ask for sensitive information over the phone. Do not provide personal, financial, or account details to the caller.Report the Call: Report the incident to your bank, local authorities, or the Federal Trade Commission (FTC). This helps to alert others and potentially track down the scammers.Educate Yourself and Others: Stay informed about the latest scam tactics and share this information with friends and family. Awareness is a key defense against fraud.If you need assistance or have concerns about potential scams, dont hesitate to seek help. At The Oberon House in Arvada, CO, we prioritize the safety and security of our residents. Contact us today to ensure your loved ones are in a safe space 303-420-7258!
Ways Seniors Can Avoid Online Shopping Scams
Online shopping has become a convenient way for seniors to purchase everything from groceries to gifts. However, with the rise in online transactions, theres also an increase in scams targeting older adults. These scams can lead to significant financial loss and personal information breaches.Heres how seniors can recognize these scams and shop online with confidence.Recognizing Common Online Shopping ScamsThe first step to avoiding online shopping scams is to be aware of them. Here are a few common ones: Phishing Scams: These involve fraudulent emails or messages that appear to be from legitimate companies and ask for personal or financial information. These emails often contain links to fake websites designed to steal sensitive data. Fake Online Stores: Scammers create fake websites resembling legitimate online stores to lure shoppers. These sites may offer products at unusually low prices or request personal information to complete a purchase. Auction Scams: Online auction scams involve sellers who promise goods at a bargain but deliver nothing or send counterfeit items. The payment is often requested via unconventional methods, which can be challenging to trace. Identity Theft: Fraudsters may use online shopping sites to collect personal information such as Social Security numbers, credit card details, or addresses, which they can then use for identity theft.Tips for Safe Online ShoppingHere are some practical tips for seniors to ensure a safe online shopping experience:Verify the WebsiteBefore making a purchase, verify if the website is legitimate. Look for indicators such as a secure connection (check for https in the URL), a physical address, and contact information. Avoid sites with poor design, numerous pop-ups, or spelling errors, which can be red flags for scams.Use Trusted RetailersShop from well-known and reputable retailers. Major retailers and established online stores have security measures to protect customer information. If unsure about a lesser-known site, research reviews and ratings before proceeding.Check for Reviews and RatingsReading reviews and ratings from other customers can help determine the reliability of a website or product. Look for reviews on independent platforms and avoid those that seem overly positive or generic.Protect Personal InformationShare personal or financial information only through secured channels or with familiar websites. Legitimate retailers will not ask for sensitive details via email or social media. Be cautious of requests for personal information or payment methods outside standard practices.Use Secure Payment MethodsUse secure payment methods such as credit cards or well-known payment services (e.g., PayPal) when making purchases. These methods offer fraud protection and can help resolve disputes if there are issues with the transaction.Monitor Your AccountsCheck your bank and credit card statements regularly for unauthorized transactions. Promptly report any suspicious activity to your bank to minimize potential damage.Keep Software UpdatedEnsure that your computer, smartphone, and security software are up-to-date. Regular updates help protect against malware, viruses, and other cyber threats that could compromise your personal information.Seek Help If NeededIf youre unsure about an online transaction or encounter a suspicious website, seek help from a trusted family member or friend. They can help verify the sites legitimacy or offer guidance on safe shopping practices.Online shopping can offer convenience and accessibility, but its important to remain vigilant amidst scams. At The Oberon House in Arvada, CO, were dedicated to helping our community navigate these challenges and ensuring secure and enjoyable experiences. Contact us today to learn more 303-420-7258.